- Oct 3, 2025:
- Added a Data Query Service section, which solves the ban issue fromspamhausfrom public DNS connections.
A Realtime Block List (RBL) is a list of addresses that an RBL list supplier believes are a source of Spam.
- Download qmail-dnsbl patch
- Code and logic from
rblsmtpdandqmail-dnsblpatch by Fabio Busatto - Added support for welcomelists, TXT and A queries, configurable return codes 451 or 553 with custom messages (by Luca Franceschini)
This patch replaces the djb's rblsmtpd program. It incorporates into qmail-smtpd the RBL stuff with the advantage that you can see the envelope in the logs. Registering the envelope as well as the sender ip is important to always know what happened to not received messages.
An additional improvement with respect to the use of the RBL filter *before* qmail-smtpd as rblsmtpd did is that the authenticated users who want to send messages from a remote dynamic IP will not be banned; this means that we are able to switch on the filter on the 587 submission port as well :)
To activate the RBL check just add your favourite block lists in the dnsbllist control file (one per line).
cat > /var/qmail/control/dnsbllist << __EOF__ -b.barracudacentral.org -zen.spamhaus.org -psbl.surriel.com -bl.spamcop.net __EOF__
Now restart qmail and check that the RBL lists have been parsed:
> qmailctl restart > qmail-showctl |grep dnsbl dnsbllist: List at -zen.spamhaus.org configured for dnsbl check. List at -b.barracudacentral.org configured for dnsbl check. List at -psbl.surriel.com configured for dnsbl check. List at -bl.spamcop.net configured for dnsbl check.
Improvements with respect to the original qmail-dnsbl patch
- default file
control/dnsbllistcan be overridden with env variable DNSBLLIST - if DNSBLSKIP env variable is set, qmail-smtpd skips the rbl check
- if
control/dnsblfailclosedor DNSBLFAILCLOSED are defined,qmail-smtpdconsiders the source ip as blocked even in case of lookup failures (checkrblsmtpdman page for more details) - support for environment variable RBLSMTPD (check
rblsmtpdman page for more details) - dnsbllist can contain empty lines and comments with '#' at start or end of lines; leading and trailing spaces are automatically removed
Examples and formats
Query rbl for TXT records, return code 451: "451 http://www.spamhaus.org/query/bl?ip=30.50.20.3"
zen.spamhaus.org
Query rbl for TXT records, return code 553: "553 http://www.spamhaus.org/query/bl?ip=30.50.20.3"
-zen.spamhaus.org
Query rbl for A records, custom return message with ret code 451: "451 Message rejected"
zen.spamhaus.org:Message rejected
Query rbl for A records, custom return message with ret code 553: "553 Message rejected", the following syntaxes are allowed:
-zen.spamhaus.org:Message rejected zen.spamhaus.org:-Message rejected -zen.spamhaus.org:-Message rejected
Query rbl for A records, custom return message with IP variable, replaced by remote ip:
zen.spamhaus.org:Message blocked from %IP%
dns welcomelist A query:
+welcome.dnsbl.local:welcomelist test +welcome.dnsbl.local
The following syntaxes are NOT ALLOWED:
zen.spamhaus.org: zen.spamhaus.org:-
Howto avoid being "cut off" by spamhaus.org
At the end of this guide I will show how to set up fail2ban in order to ban malicious IPs and then decrease the amount of connections to the RBL lists, avoiding to be banned consequently.
As an alternative, you may be interested to take a look to the idea of Costel Balta, which is addressed to solve the same problem.
One thing to pay close attention to when configuring the servers is avoiding to use public dns like google's 8.8.8.8 to resolve their services (more info here). This will cause a cut off due to the fact that they cannot measure our load of traffic on their servers if you use a public dns.
Data Query Service (DQS)
Using an open DNS resolver like google's 8.8.8.8 makes Spamhaus block our queries. In the SpamAssassin's headear we'll have:
0.0 URIBL_DBL_BLOCKED_OPENDNS ADMINISTRATOR NOTICE: The query to dbl.spamhaus.org was blocked due to usage of an open resolver.
The Data Query Service (DQS) allows to send authenticated queries by means of a DQS Key. It's free for servers with low traffic and it offers a trial period of 30 days.
Subscribe your account here, then navigate to the page Products->Data Query Service and create your DQS Key:
Supposing that your key is xxxxxxxxxxxxxxxxxxxxxxx, change the setting in control/dnsbllist in this way
-xxxxxxxxxxxxxxxxxxxxxxx.zen.dq.spamhaus.net
Be aware that the tld domain is now .net (it was .org for the free service).
Installing the plugin for SpamaAssassin
First of all let's disable the ordinary queries by adding the following to /etc/mail/spamassassin/local.cf:
# disable Spamhaus score URIBL_DBL_SPAM 0 score URIBL_DBL_PHISH 0 score URIBL_DBL_MALWARE 0 score URIBL_DBL_ABUSE 0 score URIBL_DBL_ABUSE_REDIR 0 score URIBL_DBL_ABUSE_PHISH 0 score URIBL_DBL_ABUSE_MALWARE 0 score URIBL_DBL_BLOCKED 0 score URIBL_DBL_BLOCKED_OPENDNS 0 # disable DNSWL score RCVD_IN_DNSWL_BLOCKED 0 score RCVD_IN_DNSWL_MED 0 score RCVD_IN_DNSWL_HI 0 score RCVD_IN_DNSWL_LOW 0
Download the latest package:
git clone https://github.com/spamhaus/spamassassin-dqs
Things go in a slightly different way when the HBL dataset is enabled (it's not enabled for free accounts).
Enter the 4.0.0+ folder and run the test to confirm that our key is valid also for HBL (this doesn't mean that it's enabled as well):
sh hbltest.sh Please input your DQS key: xxxxxxxxxxxxxxxxxxxxxxxxxxxx Looking up test record for HBL... done Your DQS key xxxxxxxxxxxxxxxxxxxxxxxxxxxx is enabled for HBL You can copy sh_hbl.cf and sh_hbl_scores.cf if you want HBL enabled
Now you have to insert the content of the key in a couple of config files (replace xxxxxxxxxxxxxxxxxxxxxxxxx with the content of the key):
sed -i -e 's/your_DQS_key/xxxxxxxxxxxxxxxxxxxxxxxxxxx/g' sh.cf sed -i -e 's/your_DQS_key/xxxxxxxxxxxxxxxxxxxxxxxxxxx/g' sh_hbl.cf
For FreeBSD users the commands are the following:
sed -i "" -e 's/your_DQS_key/xxxxxxxxxxxxxxxxxxxxxxxx/g' sh.cf sed -i "" -e 's/your_DQS_key/xxxxxxxxxxxxxxxxxxxxxxxx/g' sh_hbl.cf
If HBL is not enabled, you can just copy the two following files in the SpamAssassin's configuration directory:
cp sh.cf sh_scores.cf /etc/mail/spamassassin
Now proceed below in the test sction.
If HBL is enabled, edit the file sh.pre in the first line:
loadplugin Mail::SpamAssassin::Plugin::SH <config_directory>/SH.pm
Now replace <config_directory> with the config dir, which is /etc/mail/spamassassin. Therefore the line becomes:
loadplugin Mail::SpamAssassin::Plugin::SH /etc/mail/spamassassin/SH.pm
If HBL is enabled, assuming that the config dir is sia /etc/mail/spamassassin, copy there the config files:
cp SH.pm sh.cf sh_scores.cf sh_hbl.cf sh_hbl_scores.cf sh.pre /etc/mail/spamassassin
Now enable HBL by editing the file /etc/mail/spamassassin/v342.pre. You have to find the line:
loadplugin Mail::SpamAssassin::Plugin::HashBL
and eventually remove the initial #.
Restart SpamAssassin:
spamdctl restart
Test the setup in this way:
spamassassin --lint
if you don't get any output then the test went well.
Testing the filter
Navigate to https://blt.spamhaus.com/ and insert a valid email address. Then add the DQS key and run the tests:
You'll get something like this:
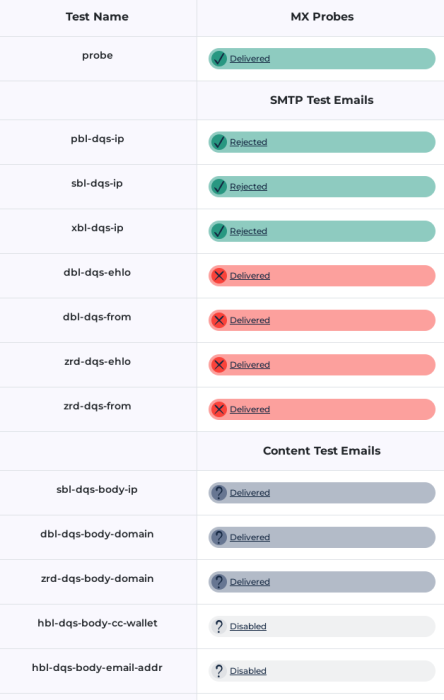
In the above example HBL is disabled, while messages with DBL ande ZRD tests apparently failed. Be sure that DBL and ZRD tests have been rejected by SpamAssassin, by checking the junk folder:
Content analysis details: (19.5 points, 5.0 required)
pts rule name description
---- ---------------------- --------------------------------------------------
0.7 SPF_HELO_SOFTFAIL SPF: HELO does not match SPF record (softfail)
-0.0 BAYES_20 BODY: Bayes spam probability is 5 to 20%
[score: 0.0573]
0.0 DMARC_MISSING Missing DMARC policy
2.8 TXREP TXREP: Score normalizing based on sender's reputation
8.0 SH_DBL_HEADERS A domain found in headers (mail from, reply-to etc..)
is listed in DBL
[dbl-dqs.blt.spamhaus.net]
8.0 SH_DBL_BODY The domain of an email address found in body is listed in
DBL
[dbl-dqs.blt.spamhaus.net]
Content analysis details: (12.1 points, 5.0 required)
pts rule name description
---- ---------------------- --------------------------------------------------
-0.0 SPF_HELO_PASS SPF: HELO matches SPF record
8.0 SH_HELO_ZRD_VERY_FRESH The domain used in the HELO string is listed
in ZRD and the domain age is between 0 and 4
hours
[zrd-dqs.blt.spamhaus.net]
-0.0 BAYES_20 BODY: Bayes spam probability is 5 to 20%
[score: 0.1579]
1.0 FORGED_SPF_HELO No description available.
0.4 KHOP_HELO_FCRDNS Relay HELO differs from its IP's reverse DNS
0.0 DMARC_MISSING Missing DMARC policy
2.7 TXREP TXREP: Score normalizing based on sender's reputation


Comments
Different zone name
Jae December 8, 2023 22:26 CET
Hello,
I am trying to use the DNSBL service truncate.gbudb.net. However, I've noticed that the zone name (truncate.gbudb.net) and the DNS server (blns0.gbudb.net) are different. This is causing some confusion for me on how to properly use this DNSBL. If I add"truncate.gbudb.net" into the list, I get an error "dnserr".
Any guidance or insights would be greatly appreciated.
Reply | Permalink
Different zone name
Roberto Puzzanghera Jae December 9, 2023 07:59 CET
Hi,
it seems that truncate.gbudb.net doesn't exist. The DNS server is different but this is normal. It doesn't have any truncate.gbudb.net record. So there's nothing you can do except wait for them to fix it
Reply | Permalink
Different zone name
Jae Roberto Puzzanghera December 9, 2023 08:04 CET
Hi
Please see below:
Reply | Permalink
Different zone name
Roberto Puzzanghera Jae December 9, 2023 08:09 CET
yes, there's no public IP related to that zone
Reply | Permalink
RBL and Bordermailer
Herbert March 17, 2023 14:01 CET
Hi Roberto,
here at our site we have a bordermailer who "prechecks" the EMails and puts a "Received" Line with its name and IP into the EMails.
So the RBL checks the IP of our Bordermailer which is of course normally not blacklisted.
Do you know a solution Where I can skip "Received" Lines in the Header for RBL checks?
Otherwise I have to disable RBL because its useless.....
Regards,
Herbert
Reply | Permalink
RBL and Bordermailer
Roberto Puzzanghera Herbert March 17, 2023 14:08 CET
Try to use DNSBLSKIP with that ip in the tcprules. Let me know...
Reply | Permalink
RBL and Bordermailer
Herbert Roberto Puzzanghera March 17, 2023 14:32 CET
....nope...not working...
I tried in smtpd run:
and/or in tcp.smtp:
same behavior with both - it completely skips RBL check then....
Regards,
Herbert
Reply | Permalink
RBL and Bordermailer
Roberto Puzzanghera Herbert March 18, 2023 14:52 CET
I did some tests and it's working as expected by declaring DNSBLSKIP in my tcp.smtp
Reply | Permalink
RBL and Bordermailer
Herbert Roberto Puzzanghera March 20, 2023 08:13 CET
Hi Roberto,
I suppose the IP 1.2.3.4 in your example is the IP of the bordermailer ?
When I put this line into tcp.smtp I get the error message:
tcprules: syntax: unable to parse this line: 1.2.3.4:DNSBLSKIP=""
Maybe my problem was not described detailed enough....
I don't want to skip RBL checking for EMail from the bordermailer!
Because all EMails have a "Received" Line with the IP from the bordermailer, I only want to SKIP this "Received" line so that the next Received line will be checked or all "Received" lines are checked.
But maybe this is impossible?
Reply | Permalink
RBL and Bordermailer
Roberto Puzzanghera Herbert March 20, 2023 08:31 CET
Yes . The syntax is correct. Double check
If your server gets the IP of the bordermailer then you can't have an rbl filter
Reply | Permalink
RBL and Bordermailer
Roberto Puzzanghera Herbert March 17, 2023 14:35 CET
I've never used it. I'll look at the code when I have some time
Reply | Permalink
RBL and Bordermailer
Herbert Roberto Puzzanghera March 17, 2023 14:36 CET
Great! Thank you!
Reply | Permalink
dnslist issue
Nic Chua May 27, 2020 09:25 CET
Hi, I have psbl.surriel.com and spamhaus in my dnslist.
I noticed that at times listed IPs are not blocked.
Take for example IP 213.142.156.102. This IP was listed multiple times on psbl.surriel.com since 2019 July. But in my log, netqmail still allows it to pass thru
My nslookup captured it correctly.
As my volume is not large, i don't think i am blocked.
Any idea what went wrong?
Thanks
nic
Reply | Permalink
dnslist issue
Marco Varanda Nic Chua October 25, 2022 21:18 CET
Hi Roberto.
Thanks for your job.
I want to tell you and your visitors, that pay attention on gateway and mail servers.
If you are using a public DNS like 8.8.8.8 or 1.1.1.1, and others, the /var/qmail/control/dnsbllist will be IGNORED.
https://www.spamhaus.com/resource-center/successfully-accessing-spamhauss-free-block-lists-using-a-public-dns/
If you got receiving LOGs ONLY bypassing dnsbllist on /var/log/qmail/smtpd/current
then you MUST change your GATEWAY, not using public DNS (now I'm using my own public IP with my own DNS Server)
and after that, dnsbllist finally will works and REJECT some IPs with bad reputation:
Thanks again !
Reply | Permalink
dnslist issue
Roberto Puzzanghera Marco Varanda October 28, 2022 12:57 CET
spamhaus started to work again here. Thanks Marco, I will add a note about this
Reply | Permalink
dnslist issue
Roberto Puzzanghera Marco Varanda October 26, 2022 15:06 CET
Good to know. Do you get any error code from spamhaus?
I disabled spamhaus a couple of years ago because they were bypassing my queries, and I hope this is the reason why. Now I changed my dns' forwarders and restored spamhaus. Let's see if it works again.
These three blocklists work well even with public dns
At any rate, just to clarify, a log message like this is not an error return code
it just means that the IP is not listed.
Reply | Permalink
dnslist issue
Nic Chua Nic Chua May 28, 2020 02:47 CET
Hi,
I don't think i am blocked at all. I received those spams and immediately do a lookup the IPs against the list.
Very strange indeed.
Looks like i will have to create a blacklist myself.
Thanks
nic
Reply | Permalink
dnslist issue
Roberto Puzzanghera Nic Chua May 28, 2020 11:58 CET
Nic, this only proves that you did the query to those block list, not that they considered your query and provided a response
Reply | Permalink
dnslist issue
Roberto Puzzanghera Nic Chua May 27, 2020 10:41 CET
Hi, I think you have been blocked by those rbl. I also don't have a very busy server, but I think that spamhaus is blocking me.
Unfortunately there is no way to check if the server has been blocked or not. Any hint on the purpose would be appreciated.
I suggest to turn on fail2ban in order to decrease the number of calls to rbl
Reply | Permalink
dnsbllist: I have no idea what this file does.
Steffen Ro▀kamp April 7, 2015 18:18 CET
Hi Roberto
First, thank you for your guide, which saved me countless hours getting our mailserver up and running!
I've got a problem though when trying to enable dnsbl like described here. I'm using your combined patch (current version as of now), but qmail seems not to recognize the dnsbllist file.
Do you have any idea what I might have missed?
Sincerely
Steffen
Reply | Permalink
Hi Steffen, it's strange..
roberto puzzanghera Steffen Ro▀kamp April 7, 2015 18:43 CET
Hi Steffen,
it's strange.. it's like you haven't patched qmail with the qmail-dnsbl patch... are you absolutely sure that you have actually patched qmail?
Reply | Permalink
OK, please discard my
Steffen Ro▀kamp roberto puzzanghera April 8, 2015 10:39 CET
OK, please discard my comment.
Issue was that I had an old (timestamp indicates it's from the qmail compile before vpopmail install and patching qmail) qmail-showctl in /usr/sbin which was beeing called...
All is fine, dnsbl working as expected. Thank you!
Reply | Permalink
Yes, I have checked the
Steffen Ro▀kamp roberto puzzanghera April 8, 2015 09:55 CET
Yes, I have checked the patched source files and they contain the patched lines.
I've also checked the compiled and installed binaries (qmail-smtpd and qmail-showctl) and they contain the dnsbllist string.
Indeed, very strange.
Reply | Permalink
Local User with Dynamic IP get banned
Marc September 16, 2014 09:54 CET
Hello Roberto,
i have the problem that local users with dynamic ips get banned from list even if i use submission port 587 with this user. Is it possible to whitelist local users? Thanks for helping.
Greetings
Marc
Reply | Permalink
outgoingip
roberto puzzanghera Marc September 16, 2014 10:39 CET
Marc, I think you can change your outgoing ip, adding it to control/outgoingip. take a look here http://notes.sagredo.eu/node/82#outgoingip
let us know if it will do the case, please
Reply | Permalink
Hi, the server has only one
Marc roberto puzzanghera September 16, 2014 11:31 CET
Hi, the server has only one ip adress - i know this outgoingip from another server which has more network interfaces and i don't think that this is the reason. The user has an dynamic ip from his dsl provider, which is on zehnaus blacklist. And i thought when he use the port 587 the RBL filter is bypassed. The log shows this:
qmail-smtpd: message rejected (qmail-dnsbl) (1.1.1.1.zen.spamhaus.org): info@localdomain.xy from 1.1.1.1 to info@localdomain.xy helo PCLokal 1.1.1.1=DynamicDSL.IP.Adress from User
You wrote in the description: RBL filter *before* qmail-smtpd as rblsmtpd did is that the authenticated users who want to send messages from a remote dynamic IP will not be banned - but in this case it get banned and i don't know why. For the moment i have deleted spamhaus from the dnsbllist file and then it works for the client. But Zenhaus catches a much amount of spam an i like to use this again. Do you have another suggestion? Thanks!
Reply | Permalink
can you post your
roberto puzzanghera Marc September 16, 2014 11:45 CET
can you post your qmail-submission run file and a smtp telnet session on 587 port?
Reply | Permalink
Telnet Output:telnet
Marc roberto puzzanghera September 16, 2014 12:22 CET
Telnet Output:
submission run file:
#!/bin/sh QMAILDUID=`id -u vpopmail` NOFILESGID=`id -g vpopmail` MAXSMTPD=`cat /var/qmail/control/concurrencyincoming` SOFTLIMIT=`cat /var/qmail/control/softlimit` # You MUST export this, otherwise you'd get a 30 sec timeout export SMTPAUTH="" # This enables greetdelay for qmail-smtpd. export SMTPD_GREETDELAY=1 export DROP_PRE_GREET=1 # This disables FORCETLS #export FORCETLS=1 # This enables chkuser export CHKUSER_START=ALWAYS # This enables simscan debug #export SIMSCAN_DEBUG=2 exec /usr/local/bin/softlimit -m "$SOFTLIMIT" \ /usr/local/bin/tcpserver -v -H -R -l 0 \ -x /home/vpopmail/etc/tcp.submission.cdb -c "$MAXSMTPD" \ -u "$QMAILDUID" -g "$NOFILESGID" 0 587 \ /var/qmail/bin/qmail-smtpd \ /home/vpopmail/bin/vchkpw /bin/true 2>&1Reply | Permalink
REALYCLIENT
roberto puzzanghera Marc September 16, 2014 12:39 CET
if you want to allow your LAN to relay without authentication, use port 25 and put your localnet in the REALYCLIENT variable inside tcp.smtp...
Reply | Permalink
auth first
roberto puzzanghera Marc September 16, 2014 12:31 CET
you are not authenticating, so it's normal that qmail-dnsbl checks for the block list and you are banned. You have to do the auth before the mail from: command, as this is not an open relay.
As an alternative you can always decide to turn off dnsbl:
Reply | Permalink
Need some more explantion
Marc roberto puzzanghera September 16, 2014 13:30 CET
Hello Roberto, thanks for helping. Just for clearing it more up to me, there is one thing that i didn't understand:
In the telnet sesion i missed the authentification, but when the user connects with his Mailclient to send the Mail, he gets forwarded to the submission run file and in this the authentification comes first or do i have to change something in the run file?
And if i want to use the DNSBLSKIP parameter i have to write the following in the submission run file?:
export RBLSMTPD=""
Thanks!
Reply | Permalink
the run file is correct
roberto puzzanghera Marc September 16, 2014 13:55 CET
the run file is correct. But you must do the auth if you want to relay with the 587 port, unless you are a RELAYCLIENT. And if you do the auth, dnsbl is turned off, so no need to use DNSBLSKIP
Anyway,
disables rblsmtpd, but we are not using it anymore, so forget.
Instead, if for some reason you want to disable qmail-dnsbl check just do this in your run file (qmail-smtpd or qmail-submission or both)
but I can assure that it works if you do the auth
EDIT:
as already said, the simplest thing to do is assign the RELAYCLIENT on port 25 to the IPs that have to do the relay without auth (localnets for instance) and force the auth on port 587, but I guess that port 587 cannot be used without authentication.
Reply | Permalink